An acceptable use policy is arguably one of the most important policies for small businesses providing access to their website or mobile application.
Indeed, it allows your business to maintain control and ensure the security of both its service and its users. Technology is a beautiful thing but there are undoubtedly many risks associated with using online services and handling personal or business data virtually.
The main threat to network security is without a doubt users taking risks or misusing technology. Thus it’s important to be diligent and regulate their use to prevent breaches and data loss.
Table of Contents
PRO TIP: Don’t waste your time and take the guesswork out of the legal jargon with this personalized acceptable use policy generator trusted by over 200,000 businesses.
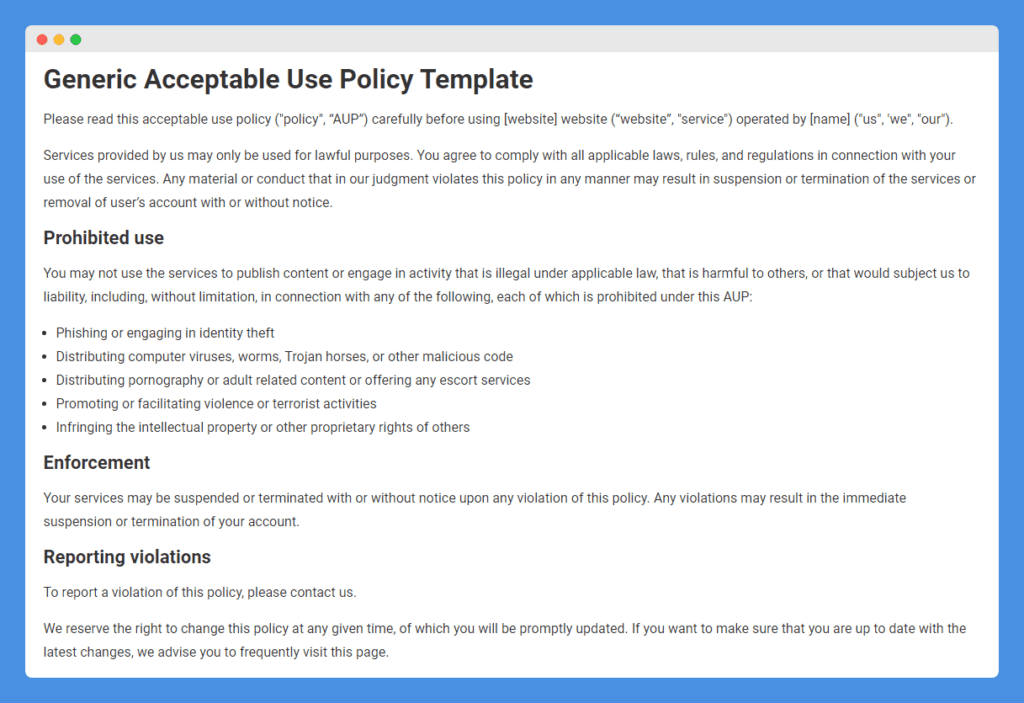
Sample Acceptable Use Policy Template
Acceptable use policies, unlike privacy policies, are not legally required and there’s no specific standard on what should be included. You need to consider the specifics and requirements of your own business, the technology you use, and your customers before drafting such a document.
This handy template is a good starting point and can be customized to your small business’ needs:
Acceptable Use Policy Examples
Online Banking Services
Transferwise, now known as Wise, is a financial technology company that allows customers to hold bank accounts in multiple currencies, apply for a multi-currency credit card, and transfer money worldwide. It does not have any physical locations, unlike traditional banks and, as such, exclusively offers its services through an online platform.
Unsurprisingly considering the risks associated with handling financial data, Wise has a detailed yet easy-to-understand Acceptable Use Policy that sets out the terms under which users can access its services (to be read in conjunction with its User Agreement which refers to its other policies).
Restricted activities
Wise starts out by stating that its services are to be used for lawful purposes only – it uses bullet points to list out prohibited uses:
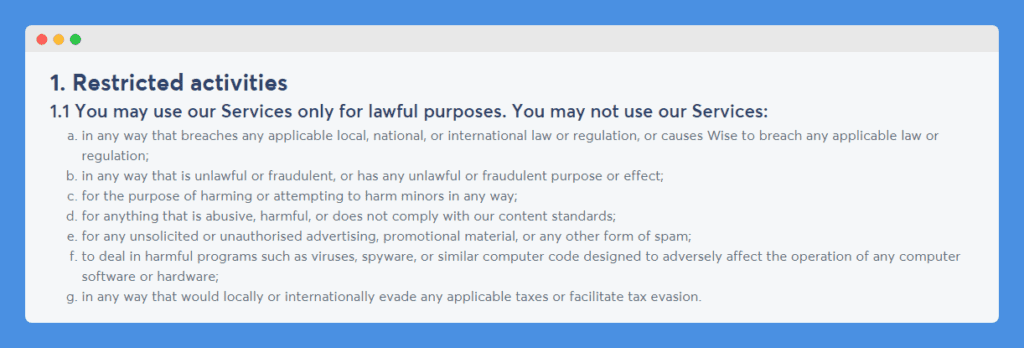
Note how general this clause is – it explains any use of its services that would breach or cause the company to breach any local, national or international laws or regulations. Being a bank, it specifically mentions that its services are not to be used for fraudulent purposes or to perform tax evasion.
Restricted businesses & transactions
In addition to restricting how its services are to be used, Wise states that it does not support a range of businesses or transactions involved in the following categories and industries as it considers them too risky:
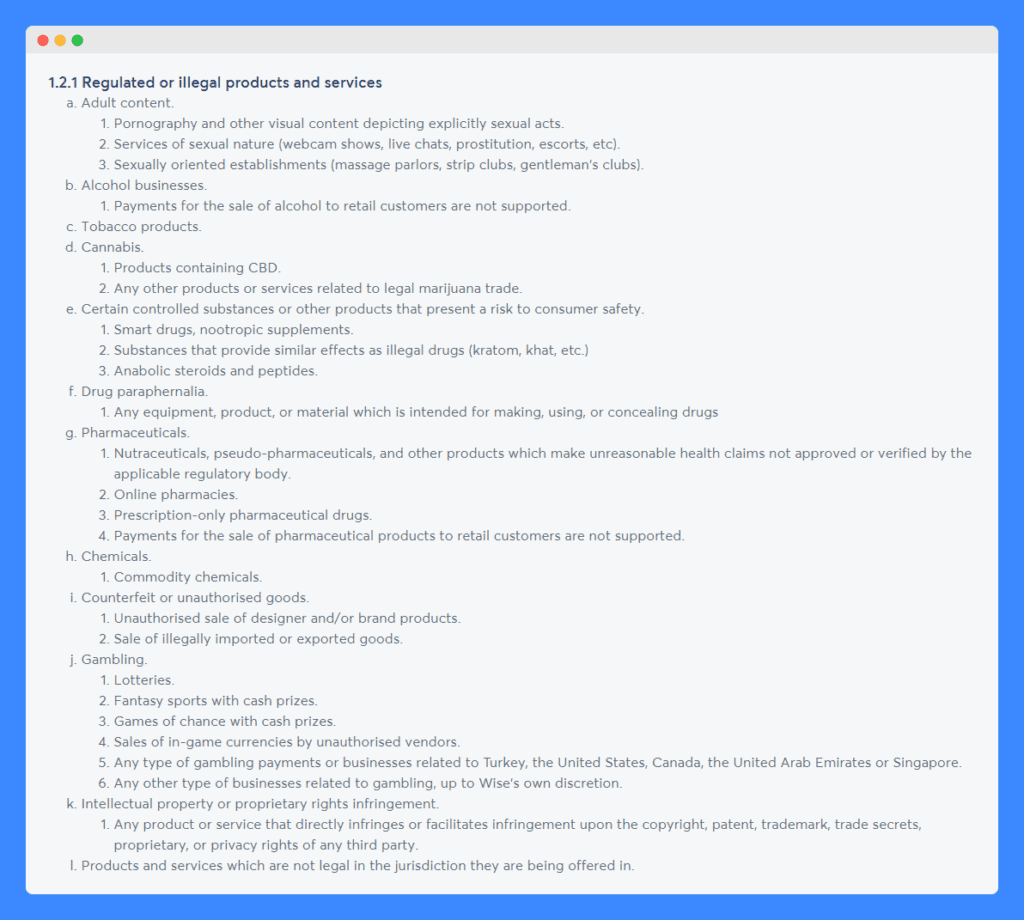
Note that this list is not exhaustive and that Wise reserves the right to deny service to any customers that it deems to exceed its risk tolerance threshold.
Penalties
Wise is very clear when it comes to explaining the consequences of not complying with its acceptable use policy.
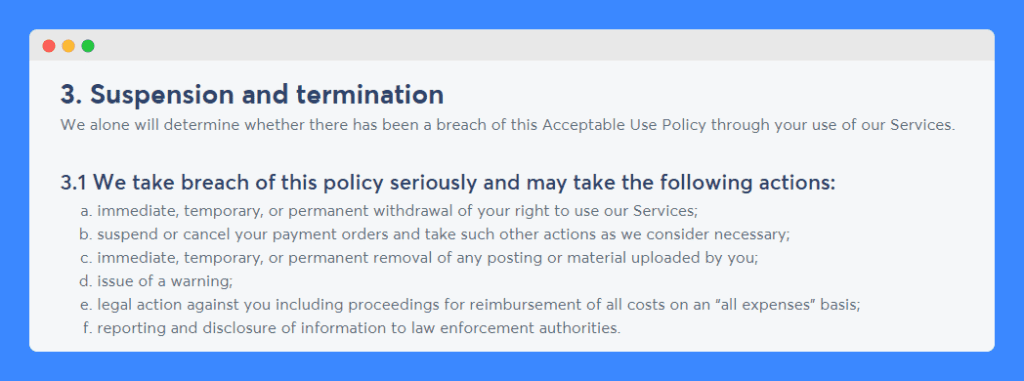
It gives itself the power to immediately remove one’s access to its services, suspend or cancel payment orders, remove user-uploaded material, issue warnings, take legal action against perpetrators and report and disclose relevant information to law enforcement authorities.
These terms should not come as a surprise to individuals that choose to use Wise’s services as they are prompted to accept them at the time of account creation:
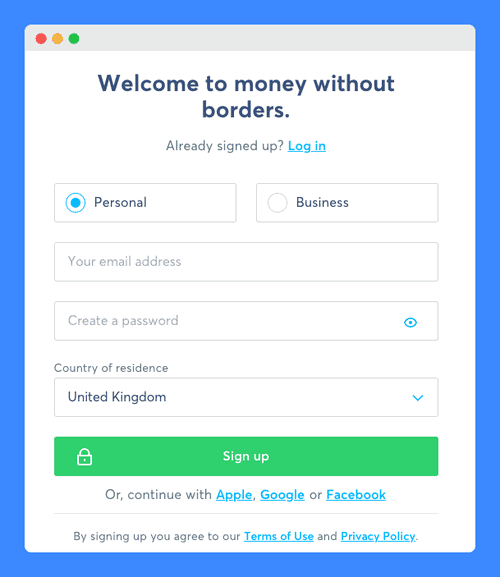
When your click on their Terms of Use link, you are taken to a page where all applicable agreements are listed and made accessible through hyperlinks, including the acceptable use policy:
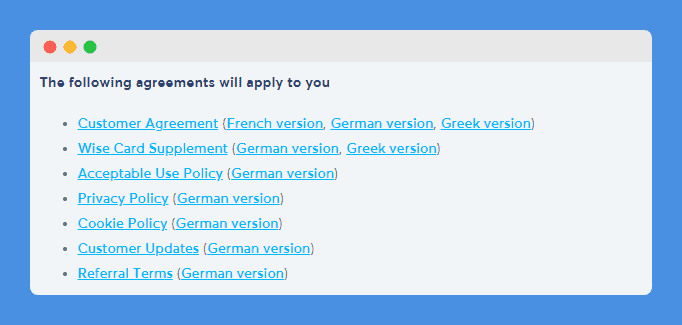
This is a great way for the company to ensure that potential customers do not miss any of the important policies that govern the use of its website and services.
Educational Institution
Prestigious Washington-based Georgetown University welcomes the finest students from all over the globe. Technology is widely used by faculty staff and students to teach, study and research and, considering the size of the institution, it has numerous strong policies in place that govern how it should be used by all.
These are all accessible in one place, through the University Information Security Office, including its Computer Systems Acceptable Use Policy.
Purpose & applicability
Perhaps to sensibilize its university population to the reason and purpose behind this policy, Georgetown University’s acceptable use document starts out by stating to whom it applies as well as the guiding principles behind it.

Note that this policy applies to anyone that uses the University’s information technology resources, and not just to students and staff.
The guiding principles are a great idea for any organization in which restrictions to technology access could be seen as a limitation of personal freedom.
The University explains that it recognizes the importance of being able to access IT resources to support education and research and to be exposed to a multitude of views. However, it does restrict usage to university-related activities only, such as research, instruction, learning, enrichment, dissemination of scholarly information, and administrative tasks.
Disclaimer
The University, by making IT resources available, is also exposing users to content that it doesn’t control, considering the amount of information that circulates on the Internet, this makes total sense. To protect itself, the University includes a disclaimer:

It also encourages users to report abuse at a dedicated email address.
Responsibilities
The University cannot possibly monitor all of the IT resources that it makes available. Thus, it sets out the responsibilities that come with choosing to use its computers or networks.
It notably reinforces the importance of taking appropriate security measures when using electronic resources, including when it comes to password management and protection from unauthorized access. It also refers users to the Georgetown University Information Security Policy which they are expected to abide by.
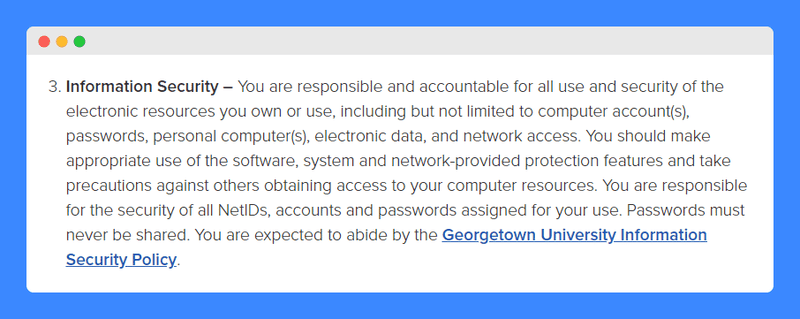
Users are personally responsible and accountable for the use and security of the electronic resources that they own or use.
It also reiterates that these are shared resources and should be treated as such:
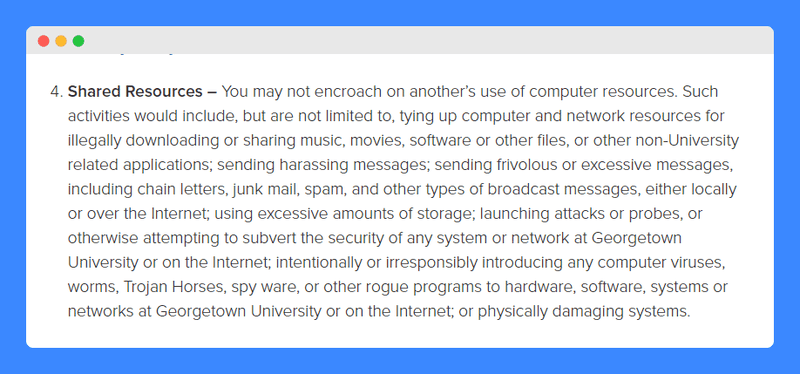
Access to those technology resources is not a right, but a privilege.
Oversight
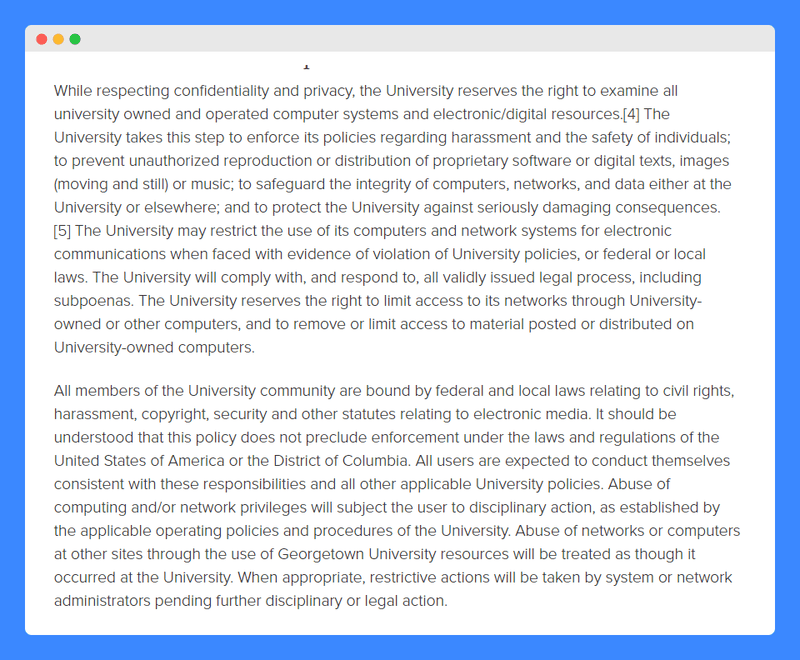
The University is very transparent when it comes to how it plans to administer and ensure compliance with this policy. It reserves the right to examine all university-owned and operated computer systems and electronic resources and to take action as needed. This can include restricting or limiting access to such technology (including its networks and the material found on its computers) when evidence of a violation is found.
Note that the University mentions that abuse could lead to disciplinary or legal action.
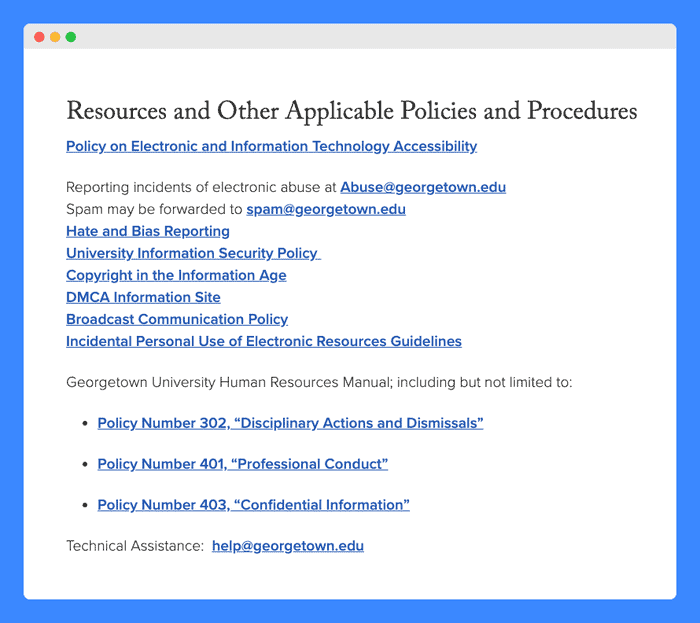
Reporting violations
Users of the University’s technology resources are invited to report incidents and abuse of this policy to a dedicated email address and to forward any spam received to another. Moreover, it includes links to other resources where hate and bias, and copyright infringement can be reported.
In addition to this acceptable use policy, the University has a separate document that applies to its employees’ incidental personal use of technology resources, the Incidental Personal Use of Electronic Resources Guidelines.
It acknowledges that sometimes employees need to use these resources for personal purposes (but should be restricted to matters that cannot wait to be addressed during non-work hours), but does specify that this should not hinder official business or affect the performance of an employee’s duties, and expressly prohibits some uses.
Network Provider
Software and network providers are probably the two types of businesses that almost without fail have a strong and detailed acceptable use policy in place.
AT&T, the world’s largest telecommunications company, is no exception. The company has a strong broadband network which it makes accessible to customers through its Internet and wireless plans.
As such, its Acceptable Use Policy applies to all AT&T services that provide or include access to the Internet or are provided over the Internet or wireless data networks (what the company refers to as “IP Services”). By using any of these services, customers confirm agreeing to comply with the company’s policy.
Prohibited uses
The policy starts off by stating all prohibited activities – here are the general prohibitions and statements concerning unlawful activities:
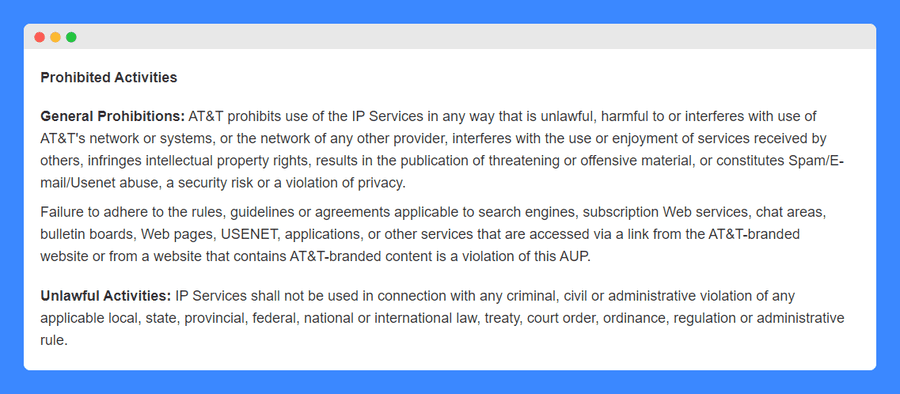
Note how it refers to and mentions all services that can be accessed through an AT&T link – customers must abide by these services’ respective rules, guidelines, or agreements in order to be found compliant with this acceptable use policy.
It then goes on to list specific prohibited uses, such as the violation of intellectual property rights, the transmission of threatening material or content, and using the services for inappropriate purposes.
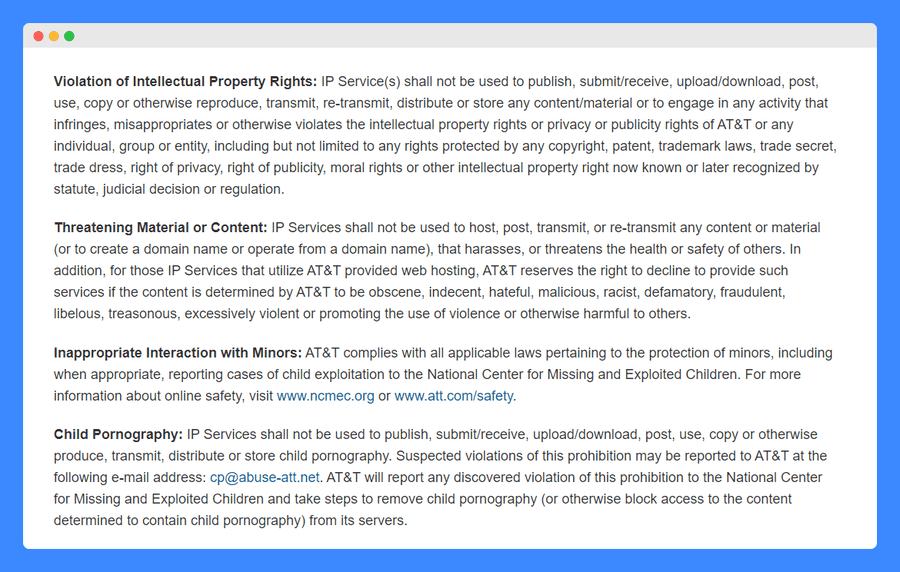
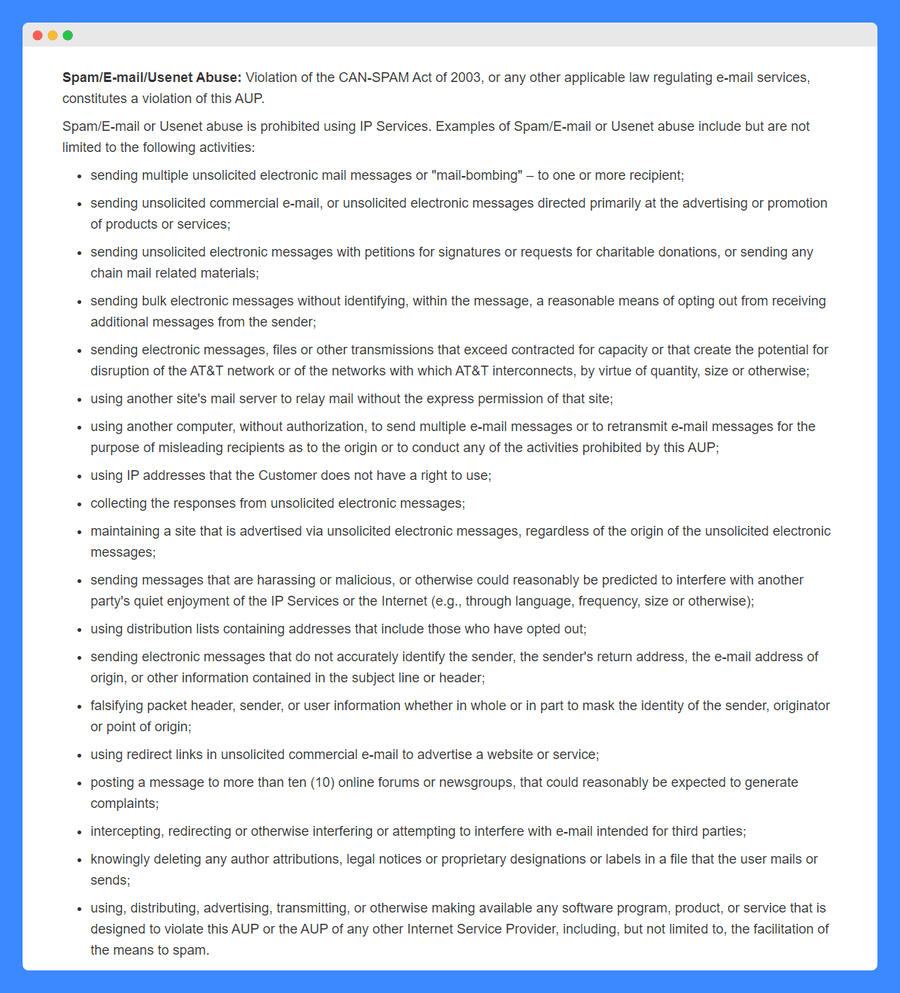
A large section of the policy is dedicated to the abuse of email services, including the sending of spam mail using its services – the list of prohibited activities is very detailed and in bullet-point form to make it easy to read:
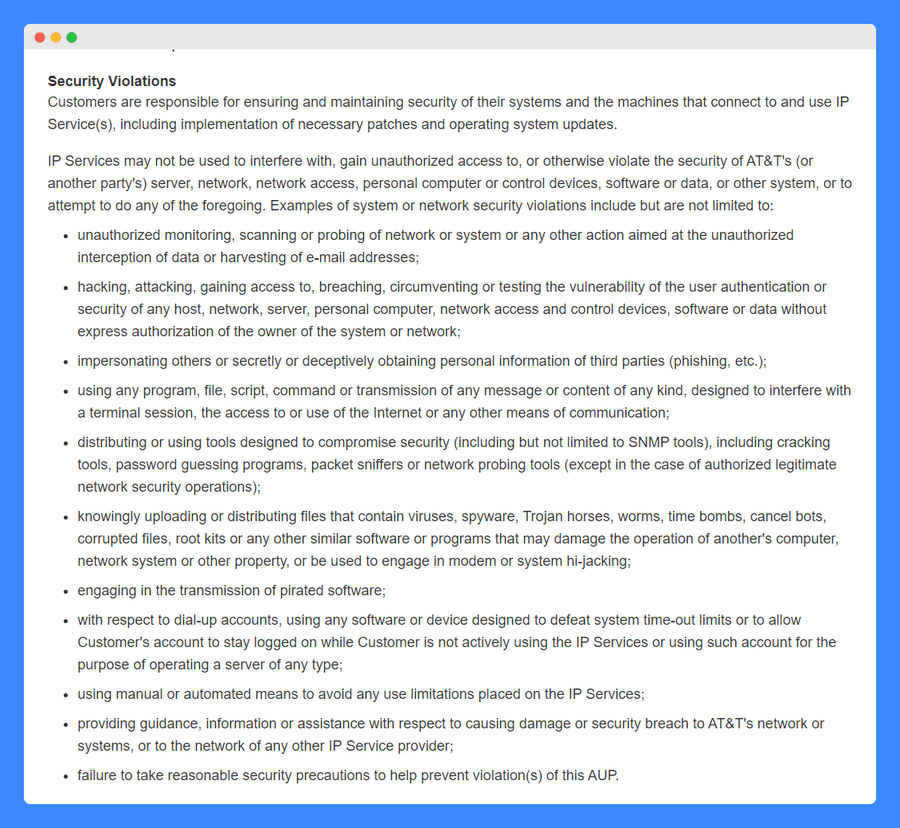
In addition, AT&T strongly condemns using its services to interfere with, gain access to or violate the security of a server, network, computer, software, or system, theirs or otherwise, and considers doing so a violation of its policy:
Responsibilities
In addition to mentioning in the clause above that ensuring the security of systems and machines that connect to AT&T’s services is the responsibility of the customer, the company states that customers remain solely and fully responsible for the content that they choose to post, host, download, upload, create, access or transmit using its services.
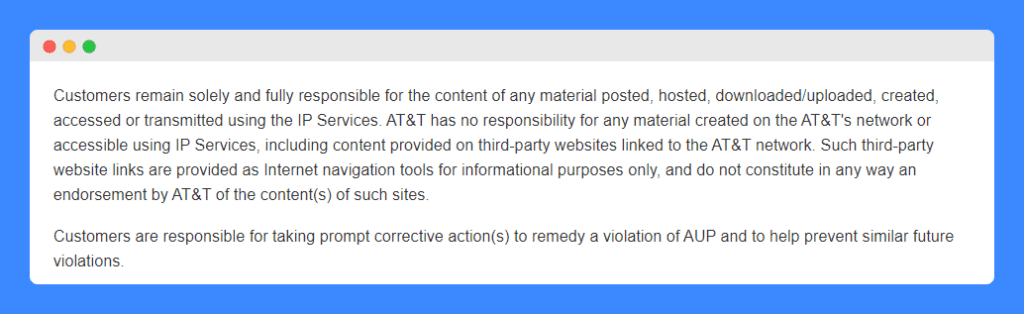
This is a standard clause for a network provider as it would be impossible and unreasonable to ask them to monitor and take responsibility for the actions of millions of customers – including such a clause makes it clear to its customers and to third parties that could be affected by their actions.
Sanctions
A few lines of AT&T’s acceptable use policy are in bold – these serve to warn customers of how the company plans to enforce this policy as well as the potential sanctions which could arise from a violation.
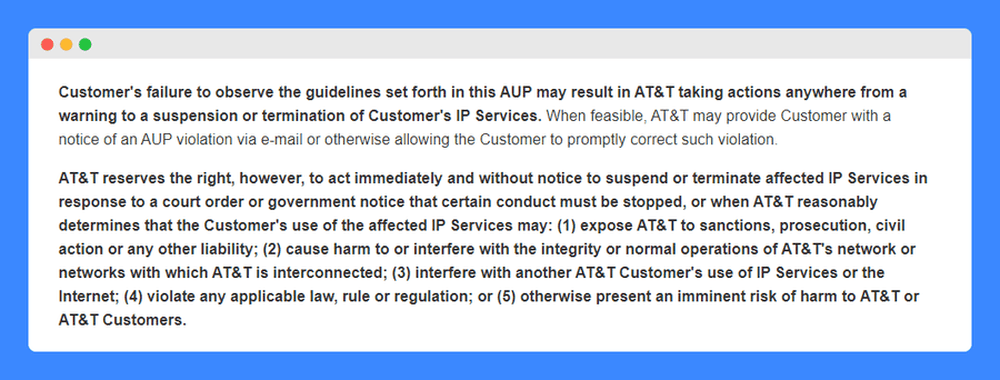
While it does state that it will warn customers of a violation when feasible to give them a chance to correct their actions, the company does reserve the right to take immediate action and suspend or terminate services in some circumstances.
These notably include when the company receives a court order or government notice or when it reasonably determines that it could expose the company to liability, harm, or interfere with the company’s network or another customer’s services, the conduct violates laws or regulations or if the use otherwise presents an imminent risk of harm to the company or its customers.
AT&T includes a clause that directly addresses copyright infringement claims and DMCA notices, as well as includes an email address where all incidents should be reported for investigation.
All in all, this constitutes a fairly standard acceptable use policy for a network provider as it addresses concerns that are specific to that type of organization.
Where Should You Display Your Acceptable Use Policy?
Where you display your acceptable use policy will depend on what kind of business you run. Common locations include:
- Your website’s footer, so it’s always accessible to users of your web-based service.
- Your legal page, which would include links to any other policies and agreements.
- Linked to from your other legal documents, such as terms and conditions.
- During the sign up process as one of the documents a new user must review and accept.
Mobile apps should include their acceptable use policy as part of the registration process, make it accessible in the menus, and display it on their business website.
Do You Need a Lawyer to Write Your Acceptable Use Policy?
No, you are not legally required to have a lawyer draft an acceptable use policy for you. With the plethora of resources and guides available, you may use a generic template or write a basic policy on your own as long as you’re willing to put in some time and effort.
Of course, depending on the complexity of your business and budget, you may want to seek legal assistance when writing your policy. For most small businesses however it’s not very practical to spend over $400/hour for a lawyer considering there are other great options available.
How to Easily Create Your Own Acceptable Use Policy?
I trust that you have found the template and examples above useful as you start thinking about drafting an acceptable use policy for your own business.
While these can serve as inspiration, you should always take into consideration the particularities of your business, customers, and the technology that you are making available.
Some acceptable and prohibited activities are fairly standard but others should directly be linked to the uses that could be made of your services as each of them has its own associated risks.
Our acceptable use policy generator is an easy and trusted solution if you want to give yourself peace of mind with a personalized policy based on your particular needs.
After all, a good policy can help you prevent abuse and retain control over your platform or services.
Once you have made your acceptable use policy available, don’t forget to update it from time to time as your organization and its privacy challenges evolve. And when you do so, take this as an opportunity to remind your users (whether they are customers, students, or employees) of its existence.