The internet is full of bad actors who will happily abuse any website or service they can find that doesn’t stop them from doing so. Whether it’s email spammers, malware distributors, botters using apps to DDoS others, or any of a thousand different kinds of hacks, unauthorized use of online services is a problem for many small businesses.
What, then, constitutes unauthorized use? If you have a web hosting company, a mobile app, a SaaS app, or any other web-based service, you’re the one who gets to define what it means.
You have to comply with certain laws and regulations, but beyond that, you’re free to determine how people can and can’t use your services.
To do this, you may create an acceptable use policy to lay out what users can and can’t do when using your products and the repercussions for misusing them.
Are you interested in learning more about acceptable use policy and how to create one of your own? Read on to find out everything you’ll need to know.
Table of Contents
PRO TIP: Don’t waste your time and take the guesswork out of the legal jargon with this personalized acceptable use policy generator trusted by over 200,000 businesses.
What is an Acceptable Use Policy?
An acceptable use policy (also known as “AUP”) is a legal document describing what is and isn’t allowed on your website, products, services, or mobile app.
It exists for two primary reasons.
- First, it serves as a notice to your customers about what they’re not allowed to do. If you prohibit certain behaviors, and a user then goes on to perform those behaviors, you are within your rights (as defined by the acceptable use policy) to suspend or remove that user’s access.
- Second, it protects you as a company against misuse of your network. Consider a service offering email sending for business newsletter management as an example. If a customer uses that app’s free trial access to send spam emails, the business risks having its sending servers blocked by other email systems.
An acceptable use policy allows the email provider to push liability to the customers misusing the system.
It allows your business to operate without worry that a customer misusing your tool can lead to lawsuits – within reason. By defining what is and isn’t acceptable use of your service, you also discourage disgruntled abusers from trying to sue you for preventing them from accessing your systems.
Is an Acceptable Use Policy Different From Terms and Conditions?
A terms and conditions agreement is a broad policy that outlines everything from user rights to data retention, intellectual property rights, payment processing, and website content.
On the other hand, an acceptable use policy is a much narrower document that focuses specifically on how your users are permitted to use your service.
In most cases, they are meant to work together and in conjunction with one another. In these cases, the terms and conditions will likely have a line like this that links to your acceptable use policy:
“The Customer agrees to abide by the terms of the acceptable use policy.”
In essence, this allows a large section of the terms and conditions to be spun off into a secondary document that can be more comprehensive. However, both documents govern the behaviors of users of your service and thus serve a similar purpose.
Creating documents for each ensures that you can keep each policy more refined and descriptive without unnecessary sprawl.
Why Do You Need an Acceptable Use Policy?
There are many benefits to having an acceptable use policy. These are all important if your business allows customers to use its platform one way or another. For example:
- It informs employees, customers, and users of the policies and terms up-front so behavior expectations are understood.
- It helps limit the liability of an organization providing a service from the misuse of that service, protecting your business or organization from potential legal action.
- It adds limits to a business service such that you can enforce it not being used for personal reasons or other uses outside the intended use case for the service.
- It can help enforce limitations on service usage to prevent individuals from over-using their “share” of resources, consuming bandwidth, storage space, or other potentially-limited resources.
- It sets standards for compliance and definitions of what a “violation” of that compliance means if a user disobeys them.
- It protects the organization’s reputation in instances of misuse of its services.
An acceptable use policy is a flexible document. It can define any range of acceptable behaviors and, conversely, prohibited behaviors when using your services.
In short, any business offering a service or product to customers can benefit from an acceptable use policy.
However, certain businesses will find an acceptable use policy to be a mandatory document. In particular:
SaaS providers
Any time you offer a web-based service to the world at large, you run the risk of bad actors using your services for various forms of abuse.
The most common issue is spam. For example, a SaaS social media management platform may wish to specify that using it to post spam, malicious comments, or links on social media violates its acceptable use policy.
Hosting providers
Web hosts are home to all websites on the internet, but malicious groups also often use them to create phishing sites, host malware, or otherwise make the internet a more dangerous place.
An acceptable use policy allows you to define abusive behavior and gives you the backing to take down sites that violate your terms.
If you are hosting illegal content without your knowledge, your acceptable use policy may also limit your liability.
Mobile app developers
In cases where a mobile app is an extension of another product or service, such as your website, that product’s acceptable use policy will generally apply.
In the case of stand-alone apps, an acceptable use policy can help you prevent common abusive use of free trials or rewards.
You also may need an acceptable use policy to comply with the general terms of the app store platforms (Apple Store, Google Play) that you use.
Online businesses
ISPs, email providers, service providers, and many other businesses can use an acceptable use policy as a supplemental document to their terms and conditions and other policies. For example, service providers like Google have acceptable use policies for services including Google Cloud and Gmail.
Many people have a misconception that an acceptable use policy is strictly meant to govern employees’ actions and access when using a business network.
While this is one use case, it’s not the only use case. As in the examples above, customers or clients are also governed by the acceptable use policy.
What Should an Acceptable Use Policy Include?
If you’ve decided that your business could benefit from an acceptable use policy, it’s time to create one. What should your acceptable use policy include?
First, it should include general rules and limitations. For example, the ActiveCampaign starts with this:
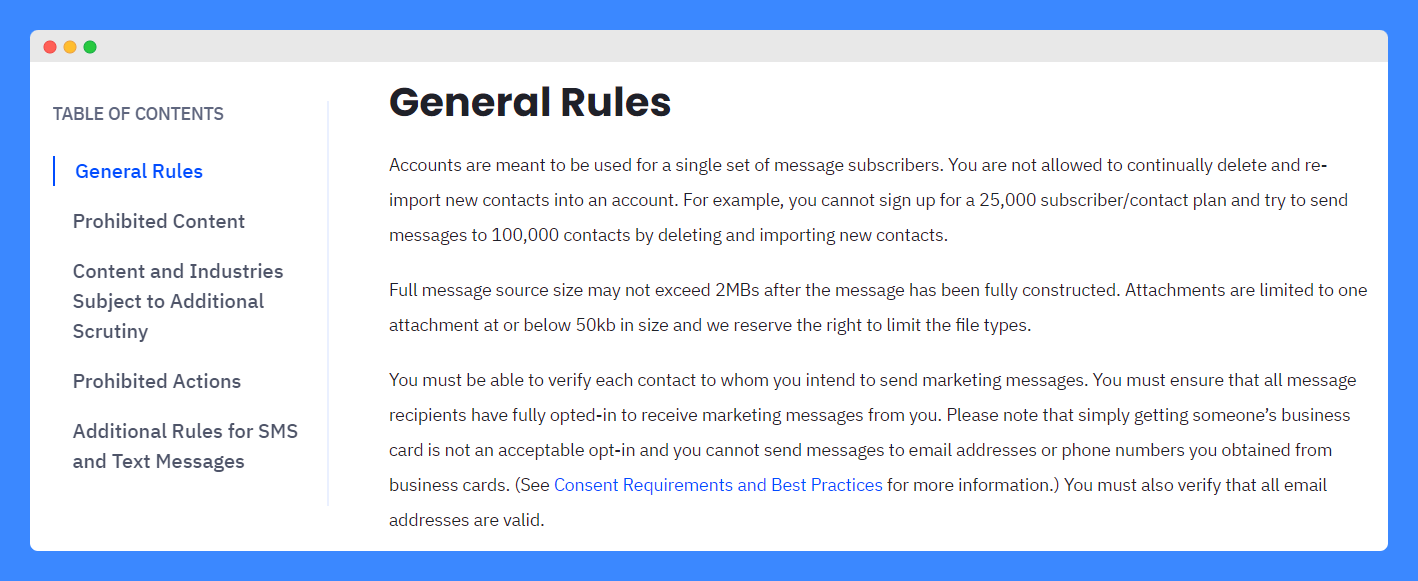
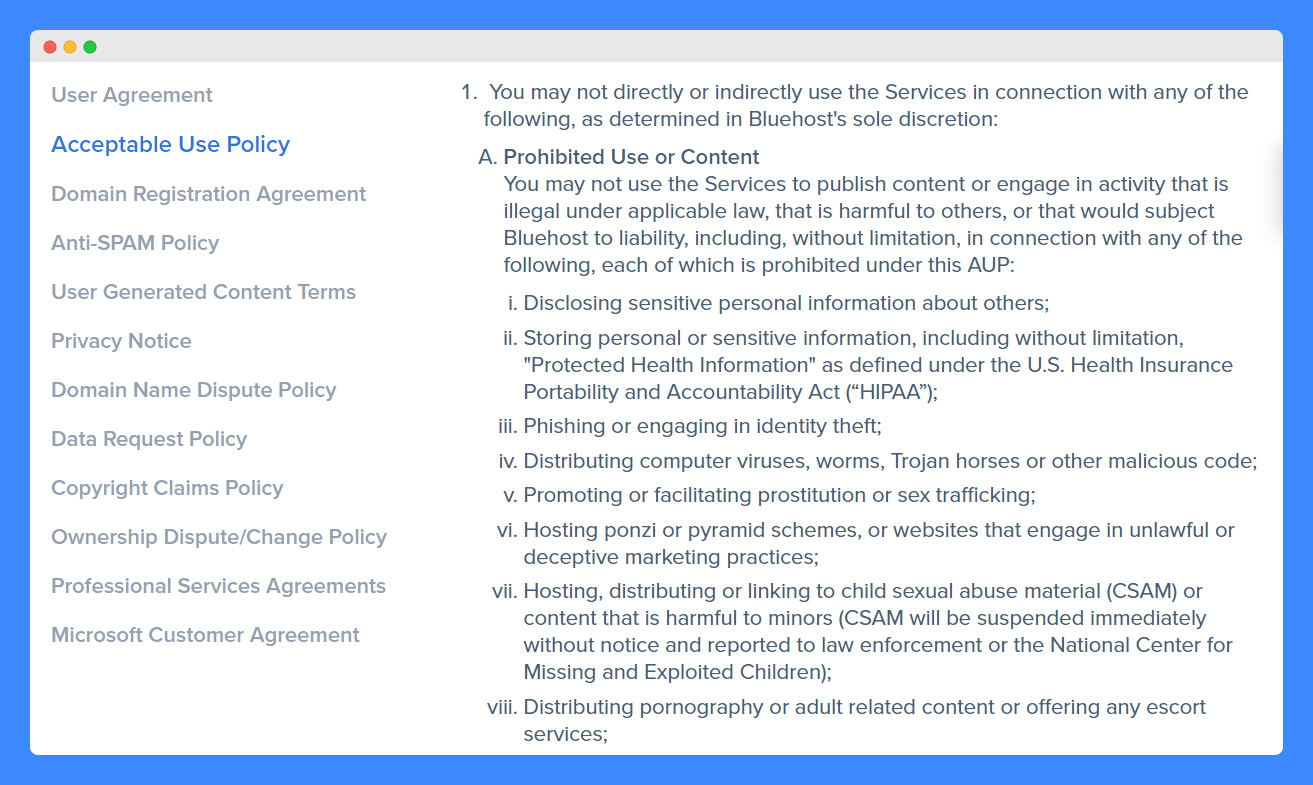
The acceptable use policy should also include your list of restricted or prohibited behaviors. A good example is Bluehost which has one for its online web hosting services:
Third, your acceptable use policy should include the potential penalties for violation of the acceptable use policy.
The acceptable use policy for Clash of Clans, a popular mobile game, outlines several “consequences of misconduct” for each section.
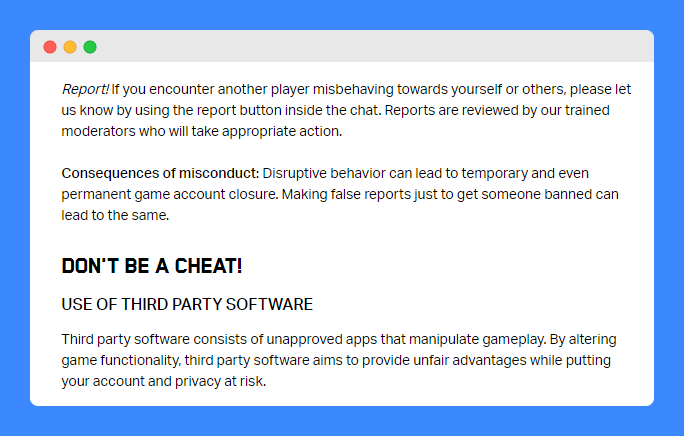
Notice how this policy in particular is rather informal in language but it doesn’t make it any less effective.
Clash of Clans is much more informal but still a relevant legal agreement.
For more examples, check out our acceptable use policy examples article.
Is an Acceptable Use Policy Required by Law?
In short, no. That said, the acceptable use policy is valuable for many businesses as a means to protect themselves.
While you may be protected against some abusive acts (for example, under Section 230 of the Communications Decency Act), you may be in a position where you need to litigate that protection. An acceptable use policy helps define liability – or lack thereof – without the need to prove it via the courts.
How to Draft Your Own Acceptable Use Policy?
There are several ways you can draft an acceptable use policy for your business. Let’s look at each one of them:
Hire a lawyer
This is an obvious choice but not a practical one for most businesses. Not only is it time-consuming, but lawyers are also notoriously expensive.
More often than not your funds will be better used elsewhere such as helping you grow your company, especially if you don’t have overly complex requirements.
Draft it yourself
There are a lot of guides and resources available online these days. If you’re willing to put in the time and effort, you may certainly draft an acceptable use policy yourself.
A big danger with this method is missing out on some important details or worse including incorrect information in your policy that could render it useless.
Use a template
Another common method is to use a generic template. You should keep in mind that you’ll likely need to personalize it to your needs as otherwise it’ll be hardly comprehensive and won’t cover important details.
Some templates may also include a lot of fluff or filler content to make them look impressive whereas in reality it adds no value whatsoever and can even do the opposite of what you’re trying to accomplish.
Use a generator
Most businesses prefer to use an online generator to create their acceptable use policy. All you need to do is fill out a questionnaire about your business and its requirements and have your policy read in minutes.
Note that, unlike the templates, a good generator will personalize the policy to your particular needs which as you already know is important.
In summary, the purpose of an acceptable use policy is to help you protect your business so be sure to create one to shield your company from bad actors, spam, and curb abuse before it’s too late.