New York City is a financial, retail, media, and tourist hub with a massive population, making its private and public institutions highly lucrative targets for malicious groups seeking to steal private information.
In 2019, the New York SHIELD Act was enacted to protect against the increasing threat of identity theft, data breaches, and cyber crimes due to longstanding gaps and inefficiencies in the state’s existing privacy law.
This article will explore the act’s scope, implications, and relevance for your business operations.
- The SHIELD Act enhances data security by expanding breach definitions and data security requirements.
- Quick and accurate data breach responses, including notifications to individuals and authorities, are of major significance under the SHIELD Act.
- The New York Attorney General enforces the SHIELD Act, imposing substantial penalties for violations, serving as a reminder of the importance of data security and ethical responsibility.
Table of Contents
PRO TIP: Don’t waste your time and take the guesswork out of the legal jargon with this personalized privacy policy generator trusted by over 200,000 businesses.
What Is the New York SHIELD Act?
The Stop Hacks and Improve Electronic Data Security Act (SHIELD Act) is a New York data security law enacted in 2019. The legislation aims to enhance the existing protection of private information by compelling businesses to implement additional measures to secure such data.
The law amends New York’s existing Information Security Breach and Notification Act, applying to any person or business that handles the private information of New York residents by requiring reasonable safeguards for data protection to ensure security, confidentiality, and integrity.
In 2016, New York Attorney General Eric T. Schneiderman reported data breach incidents have increased by 60 percent compared to the previous year, exposing the personal records of approximately 1.6 million New Yorkers. These findings underscored the urgency of implementing enhanced data protection measures in New York.
At its core, the SHIELD Act significantly changes how private information and data breaches are defined.
Private information now includes more than just the typical suspects, like social security numbers, driver’s license numbers, and credit/debit card info. Biometric data, email addresses, corresponding passwords, and security question answers are now part of the requirement.
The law has also broadened the definition of a data breach. Before, a breach was the unauthorized “acquisition” of computerized data. Now, a data breach includes any unauthorized “access” to computerized data compromising private information’s confidentiality, security, or integrity.
Businesses are obliged to implement various safeguards, including administrative, technical, and physical measures, to protect private information. They must also inform users of security breaches and notify specific state agencies within a reasonable time.
If your business handles the personal or private information of individuals residing in New York, even if your business operates outside the state, it is imperative to ensure compliance with the SHIELD Act. Otherwise, you may face investigation and legal action by the New York State Attorney General’s office.
What Are the General Definitions of the SHIELD Act?
Under the New York SHIELD Act, certain terms hold significant meanings essential for understanding the law’s scope and requirements. Let’s break down these important definitions:
- Personal Information: This term encompasses any information related to an individual that, because of their name, number, personal mark, or another identifier, can be used to identify that person.
- Private information: Under the SHIELD Act, Private information is divided into two categories. The first category includes personal information combined with specific data elements, whether encrypted or not, encompassing items like Social Security numbers, driver’s license numbers, account numbers, access details, and biometric data such as fingerprints or voiceprints. The second category involves a user’s email or username paired with a password or security question, granting access to online accounts.
- Breach of the Security of the System: This term signifies unauthorized access to or acquisition of computerized data that compromises the security, confidentiality, or integrity of the private information maintained by a business.
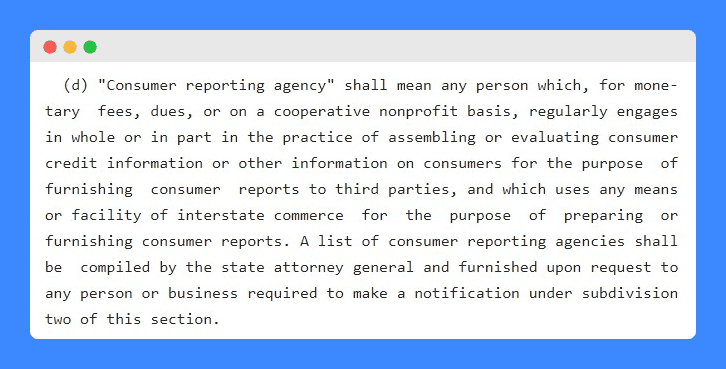
- Consumer Reporting Agency: A company that collects and evaluates information about consumers’ credit and other data. They provide reports to other businesses for a fee and use communication methods across state lines. You can get a list of these companies from the state attorney general if you need it for notifications.
Who Does the SHIELD Act Apply To?
Formerly, the law primarily targeted every business in New York handling private information. However, the SHIELD Act expands its applicability to a much wider audience.
- Businesses and Individuals: This law applies to any business and individuals who own or license computerized data containing private information of a New York resident. This inclusion of individuals underscores the law’s commitment to safeguarding personal data, irrespective of the entity controlling it.
- Geographical Reach: Previously, the law was primarily concerned with businesses physically operating within New York. Now, the law applies to individuals and businesses regardless of their physical location or whether they conduct business within New York. This means that if you hold private information of New York residents, you are subject to the SHIELD Act’s provisions, regardless of where you are based.
- Emphasis on Privacy Protection: The SHIELD Act recognizes that personal data is frequently stored and accessed across borders in today’s interconnected world. Consequently, it takes a proactive approach by requiring companies to implement a data security program regardless of location.
The SHIELD Act casts a wider net, pushing companies to maintain reasonable safeguards to protect private data. Whether you’re a business owner or an individual, understanding and complying with the law’s requirements is essential to protect your interests and New York residents’ sensitive information.
How Can Businesses Comply With the SHIELD Act?
To navigate the complexities of the SHIELD Act effectively, businesses can follow a structured approach to compliance. Here, we break down the steps in a straightforward manner, offering context at each stage to help businesses ensure compliance with this important legislation:
1. Understand the Expanded Data Breach Definitions
Under the updated definition, a breach is not limited solely to the unauthorized “acquisition” of data but extends to encompass any unauthorized “access” to computerized data. This expansion reflects the evolving landscape of data threats in our digital age.
When data is said to have been “accessed,” it typically means that there are indications the information has undergone one or more of the following actions:
- Viewed: Unauthorized individuals may have viewed the data, potentially compromising its confidentiality.
- Communicated With: There may have been unauthorized communication with the data, suggesting potential security breaches.
- Altered: Unauthorized alterations or changes to the data may have occurred, raising concerns about data integrity.
On the other hand, signs that information may have been “acquired” encompass situations where:
- Loss or Theft: A computer or device containing sensitive data is lost or stolen, potentially leading to unauthorized access.
- Downloads or Copies: Evidence suggests that the information has been downloaded, copied, or duplicated, raising concerns about data security.
- Identity Theft Reports: Reports of identity theft involving that specific information may surface, indicating potential misuse.
2. Identify Private Information Your Business Handles
The SHIELD Act also expands the definition of Private information.
Private information is divided into two categories:
Scenario I: Personal information combined with specific data elements, when either the data element or the combination of personal information plus the data element is not encrypted or if it is encrypted with an encryption key that has also been accessed or acquired. This includes:
- Social Security numbers.
- Driver’s license numbers or non-driver identification card numbers.
- Account numbers, credit or debit card numbers, when combined with any required security code, access code, password, or other information that would grant access to someone’s financial account.
- Account numbers, credit or debit card numbers if there are circumstances where such numbers could be used to access an individual’s financial account without additional identifying information, security code, access code, or password.
- Biometric information is data generated by electronic measurements of a person’s unique physical characteristics, such as fingerprints, voice prints, retina or iris images, or other unique physical or digital representations used for identity authentication.
Scenario II: Involves a user’s email or username paired with a password or security question, granting access to online accounts.
Private information does not include publicly available information and is lawfully accessible to the general public through federal, state, or local government records.
3. Implement a Comprehensive Data Security Program
The SHIELD Act requires the implementation of robust data safeguards to protect the private information of New York residents. This encompasses administrative, technical, and physical measures. While the Act provides a foundational framework, it’s essential to recognize that the listed safeguards are not exhaustive, encouraging specialized security practices to address unique business needs.
Administrative Safeguards:
- Designating Security Personnel: One key administrative measure involves designating one or more employees responsible for coordinating the security program.
- Risk Assessment: Identifying reasonably foreseeable internal and external risks is fundamental. This involves comprehensively evaluating potential threats and vulnerabilities that could compromise data security.
- Evaluating Safeguards: It’s essential to continually assess the sufficiency of existing safeguards to control the identified risks. Regular evaluations help ensure that security measures remain effective.
- Employee Training: Training and managing employees in the practices and procedures of the security program are important. Employees are often the first line of defense against security breaches.
- Vendor Oversight: Selecting service providers capable of maintaining appropriate safeguards and requiring these safeguards through contractual agreements is vital for securing third-party interactions.
- Adaptive Security Programs: The Act emphasizes the importance of adjusting the security program in light of business changes or new circumstances. Flexibility and adaptability are key components of an effective security strategy.
Technical Safeguards:
- Network and Software Assessment: Assessing network and software design risks is important. This evaluation ensures that the system’s architecture identifies and addresses potential vulnerabilities.
- Information Processing and Storage: Risk assessment should also extend to information processing, transmission, and storage, covering the entire data lifecycle.
- Threat Detection and Response: Implementing mechanisms for detecting, preventing, and responding to attacks or system failures is necessary for proactive security measures.
- Regular Testing and Monitoring: Regular testing and monitoring of the effectiveness of key controls, systems, and procedures helps maintain a strong security posture and adapt to emerging threats.
Physical Safeguards:
- Storage and Disposal Risk Assessment: Assessing information storage and disposal risks is critical to physical safeguards. This includes evaluating how data is stored and destroyed.
- Intrusion Detection and Prevention: Detecting, preventing, and responding to intrusions is essential to prevent unauthorized access or tampering.
- Access Control: Protecting against unauthorized access to or use of private information, both during and after collection, transportation, and disposal, is a foundational element.
- Secure Data Disposal: Proper disposal of private information within a reasonable timeframe after it’s no longer needed for business purposes is essential. This often involves erasing electronic media to render the data unreadable or irretrievable.
4. Respond to Data Breaches Promptly
The SHIELD Act introduced significant data breach notification requirements, offering users and authorities information within a reasonable amount of time.
An obligation to issue a breach notification arises when a “breach of the security of the system” is discovered, detected, or reasonably believed to have occurred. This breach must allow unauthorized access to a system containing private information of any New York resident “without valid authorization.”
To determine if a breach has occurred, the Act recommends examining indicators such as whether the information is in the physical possession or control of an unauthorized person, if it has been downloaded or copied, or if it has been used in an unauthorized manner, such as identity theft or fraudulent account openings.
In the event of a breach, timely and reasonable notification of the following is crucial.
The SHIELD Act specifies four methods for providing breach notifications:
- Written Notice: Sending a physical written notice.
- Electronic Notice: Sending notifications electronically if the affected person has consented, with proper record-keeping.
- Telephone Notification: Making direct phone calls to affected individuals and maintaining a log of each call.
- Substitute Notice: This method may be used if costs exceed $250,000, over 500,000 individuals are affected, or the organization lacks the necessary contact information.
Regardless of the notification method, notices must contain:
- Contact information of your business
- Contact details for relevant state and federal agencies offering security breach response and identity theft prevention information.
- A description of the categories of information accessed or acquired without authorization.
The SHIELD Act also adds further reporting stipulations.
For instance, the New York Attorney General must be notified within 10 days if it is determined that the breach is unlikely to result in misuse, financial harm, or emotional harm. Alternatively, notification should be sent to the New York State Attorney General within five business days of notifying the Secretary of State when complying with HIPAA (Health Insurance Portability and Accountability Act) requirements.
What Are the Exemptions Under the SHIELD Act?
The New York SHIELD Act brings important amendments that specify notification requirements and provide exemptions, offering practical flexibility while maintaining the security of personal information.
Good Faith Access
The SHIELD Act explicitly states that no notification is required when private information is accessed or acquired in “good faith” by an employee or agent for legitimate business purposes. However, it’s important to note that this exemption does not apply if the employee or agent, in the course of business, makes an unauthorized disclosure of private information.
Mistaken Disclosure
Another exemption includes situations where an authorized person inadvertently exposes private information, but the disclosed information is unlikely to result in misuse or cause financial or emotional harm. In such cases, the company’s determination must be written and retained for at least five years.
If the data exposure affects more than 500 New York residents, this written determination must be promptly submitted to the state attorney general within 10 days.
Compliance With Federal Regulations
The SHIELD Act aligns with federal or New York state data security regulations. It removes the obligation to provide data breach notices to affected New York residents if these notices have been issued in compliance with federal laws such as the Gramm-Leach-Bliley Act (GLBA), Health Insurance Portability and Accountability Act (HIPAA), Health Information Technology for Economic and Clinical Health Act (HITECH), and/or the New York State Department of Financial Services Cybersecurity Regulation.
However, it’s essential to emphasize that the obligation to notify the New York State Attorney General, Department of State, Division of State Police, and consumer reporting agencies remains unchanged.
Email Notice Restrictions
The SHIELD Act imposes specific restrictions on the method of notifying New York residents. Email notification is no longer permissible if the private information breached includes email addresses and corresponding passwords or security questions.
Instead, companies must employ alternative distribution methods such as phones, business websites, or major statewide media.
Small Businesses
The SHIELD Act outlines different rules for small businesses. The SHIELD Act defines a small business as an entity with fewer than 50 employees, annual earnings below $3 million for the past three years, or year-end assets less than $5 million.
A small business can fulfill the SHIELD Act’s reasonable security requirement by implementing a security program with suitable administrative, technical, and physical safeguards specific to its size and complexity, nature and scope of activities, and sensitivity of the information collected.
Who Enforces the SHIELD Act?
The SHIELD Act isn’t just a set of rules on paper because multiple entities actively enforce it. Here’s a list of the entities that keep a watchful eye on compliance:
- The NY State Attorney General: This authority plays an important role in taking legal action against businesses or individuals violating the Act’s provisions. They can bring actions on behalf of the people of New York to stop breaches and impose penalties when necessary.
- New York State Department: The Department of State also gets involved in the intricate web of oversight. It’s tasked with ensuring that businesses know their obligations and work towards compliance.
- New York State Police: The Division of State Police plays a supportive role by helping coordinate responses and investigations in data breach cases, ensuring a unified approach to tackling security incidents.
- Consumer Reporting Agencies: In cases where more than 5,000 New York residents are affected, the SHIELD Act requires notifying consumer reporting agencies. These agencies are essential in helping individuals protect themselves from identity theft and related consequences.
The SHIELD Act defines consumer reporting agencies as:
What Are the Penalties for Violating the SHIELD Act?
If a person or business fails to comply with the SHIELD Act, there are penalties to pay. Here’s what you need to know:
- Injunctive Relief and Restitution: The Attorney General can seek injunctive relief and restitution against any business entity that violates the SHIELD Act. This means they can take legal action to stop violations and require businesses to compensate affected individuals for losses incurred due to the breach.
- Civil Penalties for Delayed Notification: When notifying affected parties about a data breach, timing is essential, and failure to provide timely notification can result in civil penalties. The court may impose a fine of up to $20 for each instance of failed notification, with a maximum cap of $250,000.
- Civil Penalties for Inadequate Safeguards: If your business falls short in maintaining reasonable security safeguards to protect the security of private information, be prepared to face the consequences. The court can levy civil penalties of up to $5,000 for each violation.
Examples of SHIELD Act Fines
Dunkin’ Brands, the company behind Dunkin’ Donuts and Dunkin’ restaurants, faced legal consequences due to cybersecurity failures. Between 2018 and 2019, Dunkin’ experienced attacks where hackers used stolen usernames and passwords to access customers’ rewards accounts without permission.
In response, the New York Attorney General initiated legal proceedings, asserting that Dunkin’ had breached data security policies and engaged in deceptive practices against consumers.
The consent agreement required Dunkin to pay a $650,000 penalty, notify affected customers, and reset their passwords.
This agreement emphasizes the importance of transparency regarding data security practices and necessitates Dunkin to implement an information security program encompassing technological, administrative, and physical safeguards.
How Does the SHIELD Act Compare to Other Data Privacy Laws?
Understanding the SHIELD Act’s unique features, strengths, and importance is easier when we compare it to other globally recognized data privacy laws.
The General Data Protection Regulation, commonly known as the GDPR, is a European regulation with a global reach. It targets organizations worldwide that handle the personal data of EU citizens. The SHIELD Act differs significantly from GDPR.
The European regulation mandates strict consent procedures, requires timely data breach notifications, necessitates data protection officers, and demands impact assessments. Moreover, GDPR offers extensive rights to individuals, such as the right to access, erase, and transfer their data.
The California Online Privacy Protection Act, abbreviated as CalOPPA, is another key privacy regulation. It governs any commercial website or online service operator that collects data from Californian residents, regardless of where the operator is located.
As per CalOPPA, businesses are obligated to disclose the types of personal data they collect and their intended use through a transparent privacy policy. Additionally, it empowers consumers to request information on the collected data and inquire about its deletion.
Moving north to Canada, the Personal Information Protection and Electronic Documents Act, or PIPEDA, focuses on private sector entities that commercially utilize personal information.
PIPEDA sets out guidelines for consent, data protection, and breach notifications. Unlike the SHIELD Act, PIPEDA grants individuals the right to access and correct their data. They can also file complaints, thus offering a more comprehensive range of privacy rights.
Frequently Asked Questions
What is the SHIELD Act?
The SHIELD Act, or the Stop Hacks and Improve Electronic Data Security Act, is a data security law in New York that aims to protect the private information of its residents.
Who does the SHIELD Act apply to?
The SHIELD Act applies to any person or business that handles the private information of New York residents.
Does the SHIELD Act apply to businesses outside New York?
Yes, the SHIELD Act can apply to businesses outside New York if they handle the private information of New York residents.
Who enforces compliance with the SHIELD Act?
The New York State Attorney General mainly enforces SHIELD Act compliance.
What are the penalties for violating the SHIELD Act?
Penalties for violating the SHIELD Act can include civil penalties and fines up to $250,000.
How can businesses comply with the SHIELD Act?
Businesses can comply with the SHIELD Act by implementing comprehensive data security programs and promptly responding to and notifying authorities about data breaches.