Your online presence and the data you collect from your users are necessary for your operations. Personal information is at the heart of your interactions with customers, and it is important that you know how to handle it responsibly.
However, while this data helps you create personalized experiences, it can also be misused if it falls into the wrong hands. Protecting personal information isn’t just good practice but a legal and ethical imperative.
So, if you’ve ever pondered the “who, what, when, where, and why” of personal information and its role in the long-term success of your digital endeavors, you’re in the right place.
In this article, I will walk you through the nitty-gritty of personal information, from the basics to the key details you should be aware of. I will also share the best practices for keeping it secure, explore your responsibilities and users’ rights, and clarify what you can and cannot do with this valuable asset.
- Personal information is essential for online interactions. Different types of personal information include names, emails, social media posts, and other information that can be used to identify an individual.
- Protecting personal information is a legal and ethical duty. Mishandling can lead to identity theft, individual privacy invasion, and emotional distress.
- Secure customer data to maintain trust. Use encryption, educate your team, limit access, and comply with data privacy laws to safeguard personal information effectively.
Table of Contents
PRO TIP: Take the hassle of writing your own privacy policy away with our privacy policy generator trusted by over 200,000 businesses. It’ll save you hours of work and possible costly legal mistakes.
What Is Personal Information?
Personal information is the data that identifies a person and makes your customers unique – their names, addresses, birthdays, emails, and more. It’s the information that ties them to your services, and you deal with it every day.
Now, why should you care about this or one who can be identified by this information? Why should you try to understand what personal information is?
Well, personal information is your goldmine. It’s what allows you to tailor your content, products, and services to each customer’s preferences.
It’s the key to creating a personalized and engaging online experience that keeps them coming back for more.
But here’s the catch: with great data comes great responsibility. You need to understand how personal information should be collected, used, and safeguarded, which also includes how to store personal information securely.
Your customers trust you with their data, and it’s your duty to protect it from misuse or breaches.
PRO TIP: Prioritize transparency in your data practices by creating a clear privacy policy to establish trust and help customers understand how their information is handled.
Personal Information vs Personally Identifiable Information (PII)
Personal information is a broader category that includes various data about an individual, such as their name, address, or hobbies. Personally identifiable information (PII) specifically refers to information that can be used on its own or with other information to identify, contact, or locate a single person, or to identify an individual in context.
Personal information represents the broader aspects of personal data (which is another term for personal information by the way) and is personal information every individual is likely aware of.
In contrast, personally identifiable information, often abbreviated as PII, is a subset of personal information. It’s the highly sensitive data that can directly identify someone, like their Social Security number, driver’s license, or financial account numbers.
This information is called the gold standard of personal data because if it falls into the wrong hands, it can lead to identity theft or other serious issues.
Understanding this difference is essential in the digital age, where data privacy is a hot topic. You need to recognize what kind of data you collect and handle.
By identifying information within your data streams, you can take extra precautions to protect it, ensure the highest level of security for your customers, and comply with privacy regulations.
When you neglect the distinction between personal information and PII, your business can get exposed to legal and reputational risks if you mishandle sensitive data.
Types and Examples of Personal Information
Understanding what constitutes personal data for the purposes of protecting it can help you ensure that the information collected and used is in compliance with local regulations or those abroad, regardless of whether it’s the GDPR or a different data privacy regulation in your country.
Personal information is a diverse world, and it helps to break it down into categories to understand it better. Here are some examples of different types of information and what they entail:
- Contact Information: Contact information means information that identifies an individual, including names, addresses, phone numbers, email addresses, and any basic information a website or business gathers. This publicly available information is the foundation for communication and customer interaction.
- Demographic Information: Information that relates to age, gender, marital status, and cultural or social identity is considered demographic information. It helps you know who your audience is and what they like, which makes it valuable for tailoring your content and services to your target audience.
- Financial Information: Here, we talk about money matters. It includes information like bank account numbers, credit cards, and income details, and protecting this is important to prevent scams and maintain trust.
- Employment Information: Information that can be used for hiring and job applications, or job-related data, is called employment information. An example of this information is where someone works and their job title.
- Online Behavior: Your customer’s online footprint is here – browsing history, social media stuff, and location data from smartphone apps. It helps make online experiences more personal but needs careful handling.
- Health Information: This is all about medical history, medicines, and health-related details. It’s super private and has strict rules to keep it safe.
- Social Security Number (SSN): In the US, this nine-digit number is a big deal. It’s a target for identity theft, so guard it well.
- Driver’s License Number: This is a critical piece of personal information that makes it possible to identify an individual, especially in industries like transportation.
- Passport Number: When it comes to international travel, the passport number is essential. Losing it can lead to identity theft and various complications.
- Biometric Data: This includes fingerprint and facial recognition data that can lead to the identification of someone, which are increasingly used in security and authentication systems to enhance user protection.
Each kind of personal info has its level of importance and sensitivity. Knowing these categories can help you be more aware of what you’re sharing and with whom and outline that when you write a privacy policy.
It also helps you make smart choices about data, including what to collect, how to use it, and how to protect it to protect data subjects. It’s all about finding a balance between convenience and protecting individual privacy in our data-driven world.
How Personal Information Is Defined by Data Privacy Laws
Data privacy laws vary from one country to another, and they define and protect personal information differently. Let’s take a look at a few countries and their data privacy laws.
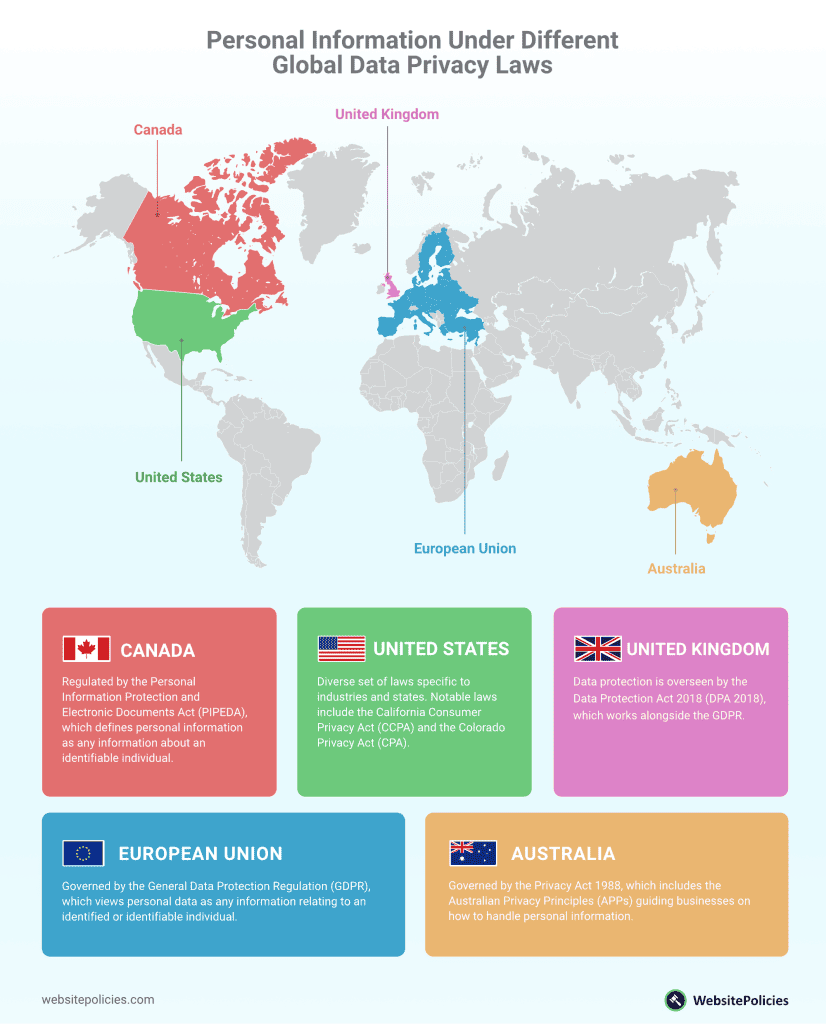
United States
In the USA, there isn’t a single comprehensive federal data protection law. Instead, various laws apply to specific industries and aspects of personal information, as well as in different states.
Personal information in the USA can include a wide range of data, from financial information regulated by laws like the GLBA to healthcare data protected by HIPAA. However, the definition of personal information varies depending on the law and the state.
For example, under the California Consumer Privacy Act (CCPA), personal information may include any information that identifies, relates to, describes, is reasonably capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household.
Meanwhile, the Colorado Privacy Act (CPA) defines personal data as information that is linked or reasonably linkable to an identified or identifiable individual.
European Union
The General Data Protection Regulation (GDPR) in the EU views personal data as any information relating to an identified or identifiable individual.
An “identifiable individual” is someone who can be identified, directly or indirectly, by reference to an identifier. This could be a name, an identification number, or even data related to their physical, physiological, genetic, or cultural characteristics.
So, if you’re collecting something as simple as an email address or IP address, that’s already within the GDPR’s purview.
Interestingly, even pseudonymized data can fall under the GDPR’s definition if there’s potential for an individual to be re-identified.
I’ve seen businesses mistakenly believe that data is safe simply because it’s pseudonymized. Remember, it’s not just about what you collect, but how it can be pieced together.
One opinion I hold strongly is that the GDPR isn’t about restricting businesses but rather about re-establishing trust. When you think about it, understanding the broad scope of “personal data” helps in reorienting your approach to data privacy.
PRO TIP: It’s always better to be on the safe side and assume any piece of data could be linked back to an individual. This mindset will serve you well in the ever-evolving landscape of data privacy laws.
Canada
The Personal Information Protection and Electronic Documents Act (PIPEDA) is Canada’s primary privacy law regulating the private sector’s collection, use, and disclosure of personal information.
PIPEDA defines personal information as any information about an identifiable individual. This is a broad definition that can include obvious things like someone’s name, address, or date of birth. However, it goes beyond these basics. For instance, an employee ID number or an individual’s race or ethnic origin are also considered personal information.
Certain types of data, such as business contact information or publicly available data, are excluded from PIPEDA’s definition of personal information.
Just because some data might seem “public,” it doesn’t mean combining it with other data won’t create a personal information profile.
Australia
Australia’s primary legislation concerning data privacy is the Privacy Act 1988, which includes the Australian Privacy Principles (APPs). These principles guide businesses and government agencies on how to handle, use, and manage personal information.
Under the Privacy Act, personal information is defined as any information or opinion about an identified individual, or an individual who is reasonably identifiable. This can be information regardless of its truth and whether it’s recorded in material form or not.
Examples might include a person’s name, signature, address, phone number, bank account details, photos, and even comments made about the individual in a database.
Furthermore, the Privacy Act also considers sensitive information, a subset of personal information, which carries a higher level of protection. This encompasses things like racial or ethnic origin, political opinions, religious beliefs, genetic and biometric data, and health information.
Even though some information may seem impersonal or insignificant on its own, when combined with other data, it could become “personal”. As such, it’s wise to be cautious and considerate when collecting and processing any kind of data.
United Kingdom
The UK’s primary legislation concerning data privacy is the Data Protection Act 2018 (DPA 2018), which works alongside the GDPR. Even post-Brexit, the UK has upheld stringent data privacy standards that closely mirror those of the GDPR.
Under the DPA 2018, personal data is defined as any information relating to an identified or identifiable individual.
An identifiable individual is one who can be identified, directly or indirectly, especially by reference to an identifier such as a name, an ID number, location data, or one or more specific factors that pertain to the physical, physiological, genetic, mental, economic, cultural, or social identity of that individual.
There’s also a so-called “special category data”, akin to the GDPR’s “sensitive data”. This data requires greater protection due to its more personal nature and includes things like race, ethnic origin, political views, religious beliefs, trade union membership, genetics, biometrics, health data, sexual orientation, and sexual life.
How Does Personal Information Get Stolen?
The theft of personal information from online businesses has unfortunately become commonplace. With the rise in digital transactions and the increasing amount of data online, cybercriminals have ample opportunities to exploit vulnerabilities.
One of the primary methods is phishing. Through deceptive emails or messages, attackers trick employees into revealing sensitive information or clicking on malicious links that install malware. Once malware is on the system, it can siphon off personal data or provide unauthorized access to secure databases.
Another method is exploiting software vulnerabilities. When businesses fail to regularly update or patch their software, they leave gaps that savvy hackers can exploit. This is especially true for older software versions that no longer receive security updates from developers.
Unsecured wireless networks also pose risks. If a business uses weak encryption or no encryption on their Wi-Fi networks, cybercriminals can easily intercept data being transmitted, gaining access to anything from login credentials to customer payment information.
Additionally, there’s the risk of insider threats. Disgruntled employees or those with malicious intentions might intentionally leak or sell personal data. Since they already have legitimate access to certain systems, their actions might go undetected for a significant amount of time.
Another common method is SQL injections where hackers manipulate a site’s database through its search box or URL input, which can lead to unauthorized access and data extraction.
It’s essential to realize that while technology continues to advance, so do the tactics of cybercriminals.
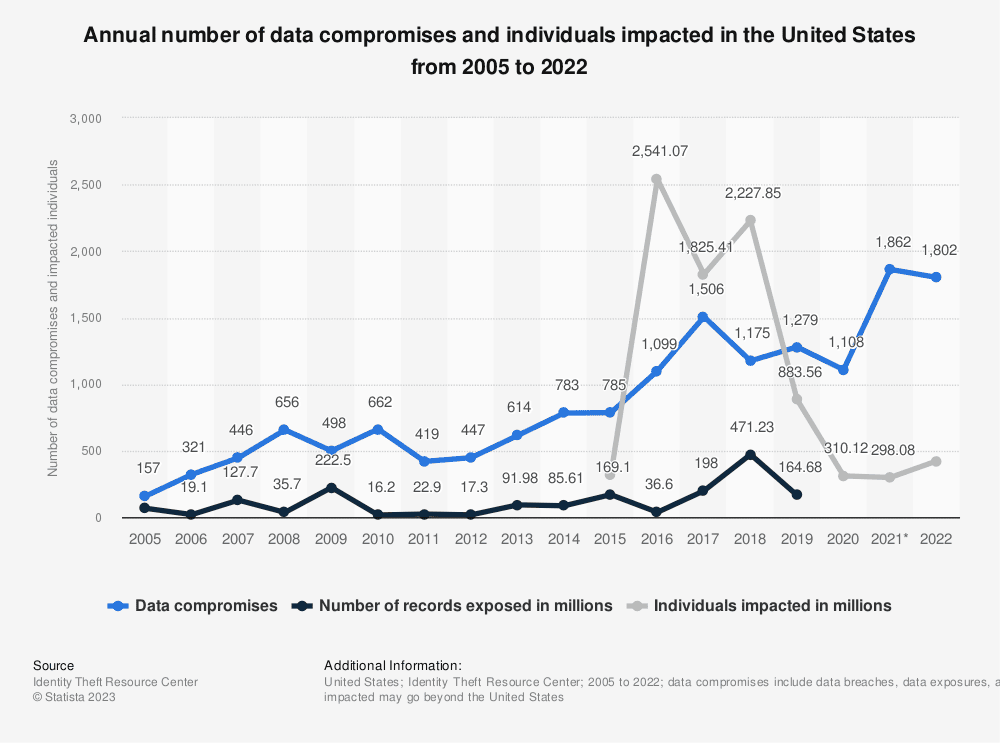
Data breaches are on the rise globally. In 2022, there were a total of 1802 cases of data compromises, which highlights the growing importance of robust cybersecurity measures.
Constant vigilance, combined with an understanding of these common threats, will go a long way in safeguarding your online business from the theft of personal information.
Consequences of Personal Information Being Stolen
When a data breach occurs, there are often substantial immediate costs. Businesses may find themselves investing in forensic experts to fully understand the extent of the breach.
They might also need to notify affected users, offer credit monitoring services, and make significant enhancements to their security measures to prevent such incidents in the future.
Beyond these immediate costs, legal fees can accumulate rapidly, especially when regulatory bodies step in. For instance, under GDPR, the penalties can be staggering, sometimes reaching into the millions or even constituting a significant percentage of a company’s annual global turnover.
But financial costs are just one piece of the puzzle. A perhaps even more challenging aspect to navigate is the reputational damage. Once customers become aware of a data breach, their trust can quickly evaporate, leading to a noticeable decline in user engagement and sales.
Moreover, in a marketplace where online privacy is highly valued, competitors with robust data protection practices could gain a distinct advantage.
Additionally, after a breach, businesses often find their focus being redirected. Instead of concentrating on growth strategies and core functions, a significant portion of their resources, both in terms of time and money, is spent managing the fallout from the breach. Even aspects like cyber liability insurance can become more costly, adding to ongoing operational expenses.
While the immediate financial losses following a data breach are evident, the long-term erosion of trust is the real cost. Reputation is invaluable in the online business landscape, and data security should be seen not merely as a technical necessity but as fundamental to sustaining business growth.
How to Protect Your Customers’ Personal Information
Protecting your customers’ personal information is both a moral obligation and a business imperative. In a digital world where data breaches are, unfortunately, all too common, taking proactive steps is essential.
Start with encryption. Whether it’s data at rest on your servers or data in transit, encryption transforms sensitive information into a code to prevent unauthorized access. I always advise businesses to keep their encryption methods up-to-date, as cyber threats constantly evolve.
Use strong, unique passwords and change them regularly. It may sound elementary, but it’s a foundational step. Encourage your customers to do the same, perhaps by implementing password strength meters or periodic password change prompts.
Regularly update your software. Cybercriminals often exploit vulnerabilities in outdated software. Make it a habit to keep all software, especially your content management system and payment processing software, updated.
Limit access. Not every employee needs access to all customer information. Assign access based on roles and responsibilities. This reduces the risk of internal data mishandling or leaks.
Educate your team. Many breaches result from human error or ignorance. Regularly train your employees about the importance of data privacy, and keep them informed about the best practices to follow.
Lastly, consider investing in a reputable cybersecurity firm or expert. They can perform regular audits, identify potential vulnerabilities, and recommend solutions.
PRO TIP: Remember, while implementing these measures may require effort and investment, the costs of not doing so, both in terms of finances and reputation can be far greater.
Frequently Asked Questions
What is personal information?
Personal information is any information relating to an identified individual or a particular person. This includes data like names, addresses, emails, etc.
What’s the difference between personal information and personally identifiable information (PII)?
Personal information is broad, while PII is data involving sensitive personal information that can be used to identify someone directly, like an SSN or driver’s license.
How do data privacy laws define personal information?
The definitions vary slightly under different data privacy laws but they generally define it as information about individuals that can directly or indirectly identify them.
What are the consequences of personal information being stolen?
Stolen personal information can lead to financial loss, identity theft, privacy invasion, and legal issues.
How can businesses protect customers’ personal information?
You can protect data by implementing secure storage, updating software, educating your team, using strong passwords, conducting security audits, and more.
What should businesses do if personal information is stolen?
If personal information is stolen, you should notify authorities, financial institutions, and credit agencies while implementing strong cybersecurity practices.